In the vast landscape of networking, terms like NAT (Network Address Translation) often come up. Among the variations of NAT, one that stands out is “Full Cone NAT.” But what exactly does Full Cone NAT mean, and why is it essential in the realm of networking? In this article, we’ll delve into the depths of Full Cone NAT, breaking down its significance, operation, and real-world implications. This article is organized by Techconnectmagazine.com.
Understanding NAT
Network Address Translation (NAT) plays a pivotal role in modern networking. It’s the mechanism that enables multiple devices within a local network to share a single public IP address for communication with external networks. NAT ensures the efficient utilization of available IP addresses while maintaining a degree of security. When it comes to NAT, there are different types such as full cone vs symmetric nat, which can affect the way devices communicate with external networks.
The Essence of Full Cone NAT
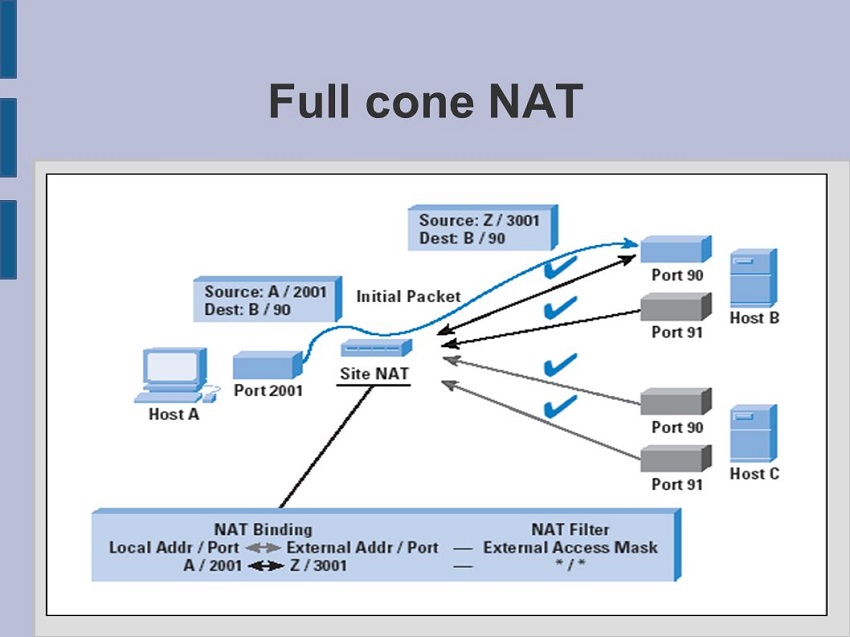
Full Cone NAT represents a particular configuration within the spectrum of NAT types. It stands as one of the most permissive forms of NAT, allowing external devices to initiate connections to internal devices using the shared public IP address. This unrestricted accessibility makes it an appealing choice for various applications, particularly in scenarios where external devices need to establish connections to servers within a local network.
How Full Cone NAT Works
Imagine your local network as a bustling city, and your public IP address as the main gateway. In Full Cone NAT, when an internal device sends out a request to an external server, the NAT device maps the internal IP address and port to a unique external IP address and port. This mapping remains consistent for the duration of the session, allowing the external server to send responses directly back to the internal device without any hindrance.
Advantages and Drawbacks
Full Cone NAT comes with its set of pros and cons. On the bright side, it simplifies communication by allowing external devices to connect seamlessly to internal resources. However, this openness also raises security concerns, as any external device can initiate communication with an internal device once the initial connection is established.
Full Cone NAT in Action: Use Cases
Full Cone NAT finds its utility in various scenarios. Online gaming, for instance, benefits from the ability to establish direct connections between players for smoother gameplay. Similarly, VoIP applications can achieve better call quality by allowing direct communication between participants.
Addressing Security Concerns
While Full Cone NAT offers convenience, its potential security vulnerabilities cannot be ignored. The ease of external initiation can be exploited by malicious entities. To counter this, various measures such as firewalls and intrusion detection systems are often employed.
Evolution and Alternatives
As technology evolves, so do networking solutions. While Full Cone NAT has its place, other NAT types like Symmetric NAT and Port Restricted NAT have emerged to strike a balance between security and accessibility. You may like to read: Which is the Fastest 2.4 GHz Option?
Full Cone NAT vs. Other NAT Types
Comparing Full Cone NAT with its counterparts sheds light on their unique attributes. Symmetric NAT, for example, restricts external devices to communicate only with the devices they initially contacted, adding an extra layer of security.
Exploring NAT Traversal
NAT traversal mechanisms have gained prominence to overcome the challenges posed by NAT types. Techniques like UPnP (Universal Plug and Play) and STUN (Session Traversal Utilities for NAT) aid in establishing connections across various NAT configurations.
The Future of Full Cone NAT
As networks continue to evolve, so will NAT solutions. Full Cone NAT might find itself coexisting with newer, more secure options. The balance between accessibility and security will remain a critical aspect of networking architecture.
Conclusion
In the intricate world of networking, Full Cone NAT stands as a bridge between accessibility and security. Its permissive nature enables direct communication between internal and external devices, facilitating smoother interactions in applications like gaming and VoIP. However, the trade-off is a potential security vulnerability that must be managed diligently through advanced security measures. As we navigate the ever-evolving landscape of technology, the role of Full Cone NAT and its counterparts will continue to shape the way we connect and communicate.
FAQs
Q1: Is Full Cone NAT the most secure NAT type?
A: No, while Full Cone NAT offers accessibility, it’s not the most secure option. Other NAT types like Symmetric NAT provide better security by restricting incoming connections.
Q2: Can Full Cone NAT be used for hosting websites?
A: Yes, Full Cone NAT can be used to host websites, as it allows external devices to connect to internal servers using the shared public IP address.
Q3: Are there any alternatives to Full Cone NAT?
A: Yes, alternatives like Symmetric NAT and Port Restricted NAT provide different levels of security and accessibility.
Q4: How does Full Cone NAT affect online privacy?
A: Full Cone NAT doesn’t directly impact online privacy. However, its security implications can indirectly affect privacy if not managed properly.
Q5: What’s the role of NAT traversal in networking?
A: NAT traversal mechanisms like UPnP and STUN help establish connections across various NAT types, ensuring smoother communication between devices.